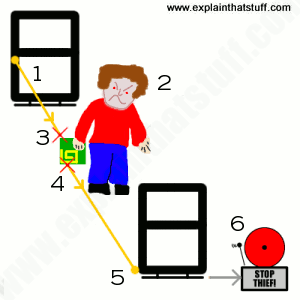
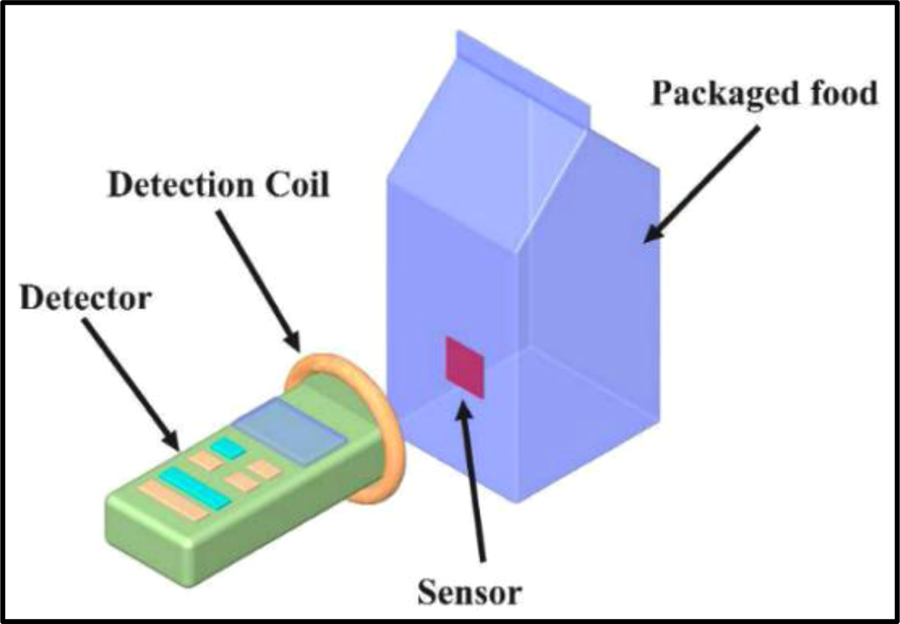
44 an rfid label on a box is an example of what type of physical security detection method
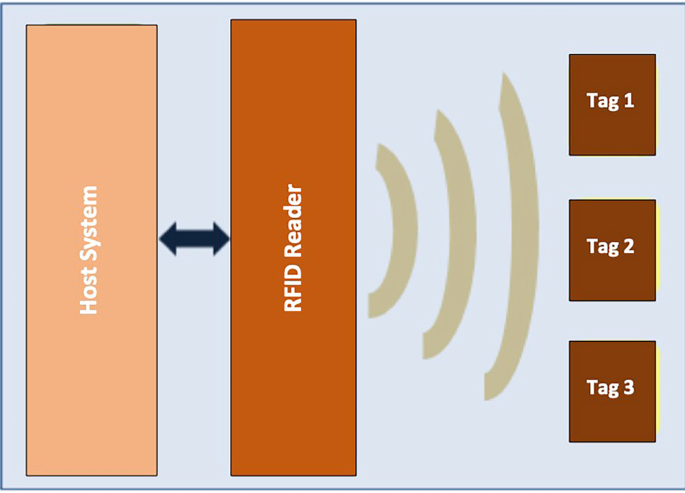
Subscribe - RFID JOURNAL Only RFID Journal provides you with the latest insights into what’s happening with the technology and standards and inside the operations of leading early adopters across all industries and around the world. To stay informed and take advantage of all of the unique resources RFID Journal offers become a member today. Introduction of Radio Frequency Identification (RFID) Radio Frequency Identification (RFID) is a method that is used to track or identify an object by radio transmission uses over the web. Data digitally encoded in an RFID tag which might be read by the reader. This device work as a tag or label during which data read from tags that are stored in the database through the reader as compared to traditional barcodes and QR codes.
RFID Tags, What Exactly are They and How do they Work? The active RFID tags come in two main types: these are transponders and beacons. Transponders are similar to the passive RFID tags wherein using the reader is required to transmit data. An information ping in every few seconds is what beacons send out. They have a signal that is readable from hundreds of feet away.
An rfid label on a box is an example of what type of physical security detection method
What are the examples of physical security? - DotNek In the following, we will give examples of physical security in more detail. Examples of physical security: - Observing biological security concerning the building: An important example of physical security is providing adequate facilities to build a secure building. To do this, you should prefer to use strong locks, anti-theft doors for the ... Success Essays - Assisting students with assignments online We care about the privacy of our clients and will never share your personal information with any third parties or persons. › playstation-userbasePlayStation userbase "significantly larger" than Xbox even if ... Oct 12, 2022 · Microsoft has responded to a list of concerns regarding its ongoing $68bn attempt to buy Activision Blizzard, as raised by the UK's Competition and Markets Authority (CMA), and come up with an ...
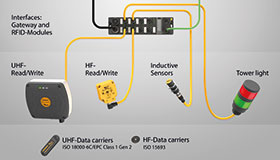
An rfid label on a box is an example of what type of physical security detection method. QR code - Wikipedia A QR code (an initialism for quick response code) is a type of matrix barcode (or two-dimensional barcode) invented in 1994 by the Japanese automotive company Denso Wave.A barcode is a machine-readable optical label that can contain information about the item to which it is attached. In practice, QR codes often contain data for a locator, identifier, or tracker that points to a … What is an RFID Label | Zebra 1) Data about the asset being tracked - This information is stored in the Electronic Power Code (EPC) memory bank. Common sizes for EPC are 96 and 128 bits but memory sizes can vary based on the microchip used 2) Data about the tag itself, such as the manufacturer 3) Data that makes the tag work, such as access and kill passwords b.) Question28 11pts what type of door access control is - Course Hero key fob lock Question 29 1 / 1 pts An RFID label on a box is an example of what type of physical security detection method? Correct! asset tracking tagging video surveillance via CCTV tamper detection motion detection technology asset tracking tagging What is RFID Labels and What Does It Consist Of? What are The Parts Of RFID Labels? RFID labels are also named RFID tags (RFID smart labels). It has three components: a microchip (IC), an antenna, and a substrate. RFID chips mainly store and process information and modulate. It can demodulate radio frequency signals. The antenna enables the RFID label to receive and send signals from the reader.
› section › newsNews articles and features | New Scientist Breaking science and technology news from around the world. Exclusive stories and expert analysis on space, technology, health, physics, life and Earth Achiever Papers - We help students improve their academic standing We are a leading online assignment help service provider. We provide assignment help in over 80 subjects. You can request for any type of assignment help from our highly qualified professional writers. All your academic needs will be taken care of as early as you need them. Place an Order Lifestyle | Daily Life | News | The Sydney Morning Herald The latest Lifestyle | Daily Life news, tips, opinion and advice from The Sydney Morning Herald covering life and relationships, beauty, fashion, health & wellbeing RFID Tag construction - what goes into an RFID tag or label An inlay consists of an IC, an antenna, attached to the substrate. Typically, the substrate does not have an adhesive. The inlays are supplied on a reel of continuous web and are used by label makers, also called converters, to embed RFID functions into labels. The continuous form of inlays helps assemble labels on high-speed equipment.
Radio-frequency identification - Wikipedia Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder, a radio receiver and transmitter.When triggered by an electromagnetic interrogation pulse from a nearby RFID reader device, the tag transmits digital data, usually an identifying inventory number, … Free Computers Flashcards about Chap 9 and 10 Quiz - StudyStack An RFID label on a box is an example of what type of physical security detection method? asset tracking tagging: What statement regarding the different versions of the SHA hashing algorithm is accurate? SHA-2 and SHA-3 both support the same hash lengths. Authentication - Wikipedia Authentication (from Greek: αὐθεντικός authentikos, "real, genuine", from αὐθέντης authentes, "author") is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity. It might involve validating personal identity ... News articles and features | New Scientist Breaking science and technology news from around the world. Exclusive stories and expert analysis on space, technology, health, physics, life and Earth
RFID Labels provide inventory visibility - Sensormatic The Sensormatic RFID 73x17mm Label delivers consistent performance and merchandise protection using RFID technology. These labels feature a highly sensitive inlay and integrated circuit to enable RFID as EAS or item-level visibility with an Electronic Product Code (EPC). Labels applied to merchandise work with RFID based EAS systems to alarm ...
en.wikipedia.org › wiki › QR_codeQR code - Wikipedia A higher security level can be attained by embedding a digital watermark or copy detection pattern into the image of the QR Code. This makes the QR Code more secure against counterfeiting attempts, and fake products which contain a counterfeit QR Code can be detected by scanning the secure QR Code with a specific app (even though the QR Code ...
en.wikipedia.org › wiki › AuthenticationAuthentication - Wikipedia The second type of authentication is comparing the attributes of the object itself to what is known about objects of that origin. For example, an art expert might look for similarities in the style of painting, check the location and form of a signature, or compare the object to an old photograph.
› lifestyleLifestyle | Daily Life | News | The Sydney Morning Herald The latest Lifestyle | Daily Life news, tips, opinion and advice from The Sydney Morning Herald covering life and relationships, beauty, fashion, health & wellbeing
What is RFID and How Does RFID Work? - ABR® RFID is an acronym for "radio-frequency identification" and refers to a technology whereby digital data encoded in RFID tags or smart labels (defined below) are captured by a reader via radio waves. RFID is similar to barcoding in that data from a tag or label are captured by a device that stores the data in a database.
IST 166 Chapter 9 Quiz - Module 9 Practice Problems Answer: True Question 5 Which of the following scenarios represents a phishing attempt? Answer: An e-mail was sent to a manager at your company that appeared to be from the company's CTO, asking for access Question 6 An RFID label on a box is an example of what type of physical security detection method?
RFID Labels - Identiv RFID TOM® (Tag On Metal) Labels Standard RFID tags are not designed for metal. The technology behind our RFID TOM® (Tag On Metal) Labels is unique. These high frequency (HF) labels (ISO/IEC 14443 or 15693) are equipped with a shielding technology that provides an optimum read range when applied to metallic surfaces. Giant NFC Labels
Network+ 8th Edition Chapter 9 Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? a. motion detection technology b. video surveillance via CCTV c. tamper detection d. asset tracking tagging d. asset tracking tagging 12.
Chapter 9 -- Network II Flashcards | Quizlet An RFID label on a box is an example of what type of physical security detection method? A) motion detection technology B) video surveillance via CCTV C) tamper detection D) asset tracking tagging. asset tracking tagging. What statement regarding the different versions of the SHA hashing algorithm is accurate?
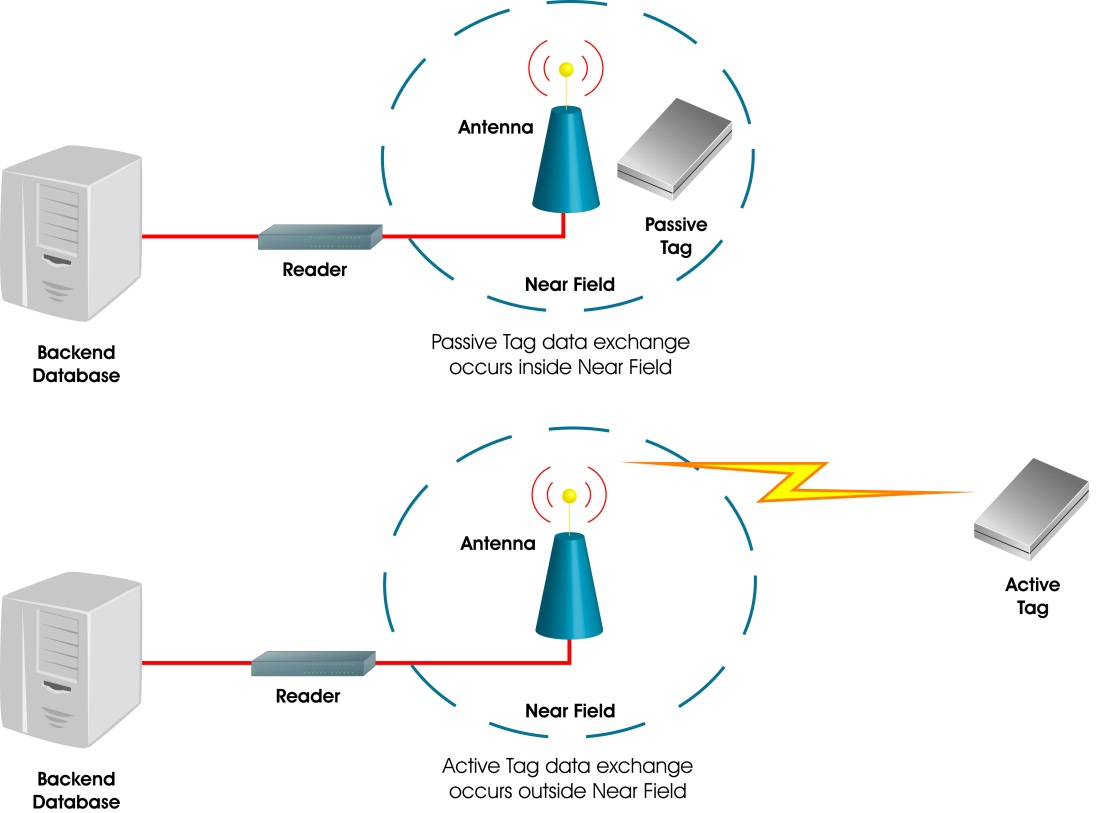
Radio Frequency Identification (RFID) | FDA The reader is a device that has one or more antennas that emit radio waves and receive signals back from the RFID tag. Tags, which use radio waves to communicate their identity and other...
PPIC Statewide Survey: Californians and Their Government Oct 26, 2022 · Key Findings. California voters have now received their mail ballots, and the November 8 general election has entered its final stage. Amid rising prices and economic uncertainty—as well as deep partisan divisions over social and political issues—Californians are processing a great deal of information to help them choose state constitutional officers and …
› subscribeSubscribe - RFID JOURNAL Only RFID Journal provides you with the latest insights into what’s happening with the technology and standards and inside the operations of leading early adopters across all industries and around the world. To stay informed and take advantage of all of the unique resources RFID Journal offers become a member today.
PlayStation userbase "significantly larger" than Xbox even if every … Oct 12, 2022 · Microsoft has responded to a list of concerns regarding its ongoing $68bn attempt to buy Activision Blizzard, as raised by the UK's Competition and Markets Authority (CMA), and come up with an ...
en.wikipedia.org › wiki › Radio-frequency_identificationRadio-frequency identification - Wikipedia Often more than one tag will respond to a tag reader, for example, many individual products with tags may be shipped in a common box or on a common pallet. Collision detection is important to allow reading of data. Two different types of protocols are used to "singulate" a particular tag, allowing its data to be read in the midst of many ...
› playstation-userbasePlayStation userbase "significantly larger" than Xbox even if ... Oct 12, 2022 · Microsoft has responded to a list of concerns regarding its ongoing $68bn attempt to buy Activision Blizzard, as raised by the UK's Competition and Markets Authority (CMA), and come up with an ...
Success Essays - Assisting students with assignments online We care about the privacy of our clients and will never share your personal information with any third parties or persons.
What are the examples of physical security? - DotNek In the following, we will give examples of physical security in more detail. Examples of physical security: - Observing biological security concerning the building: An important example of physical security is providing adequate facilities to build a secure building. To do this, you should prefer to use strong locks, anti-theft doors for the ...




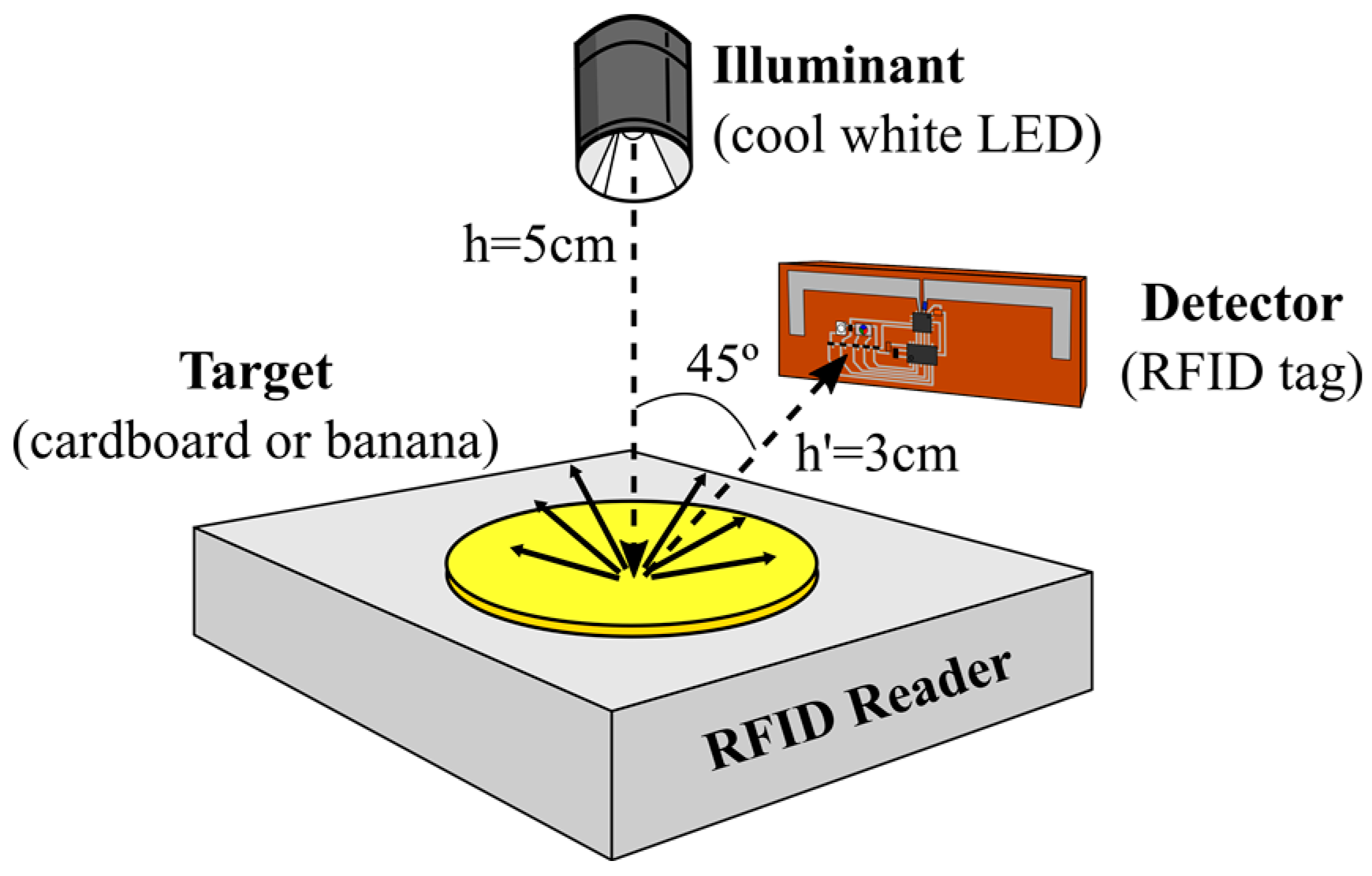


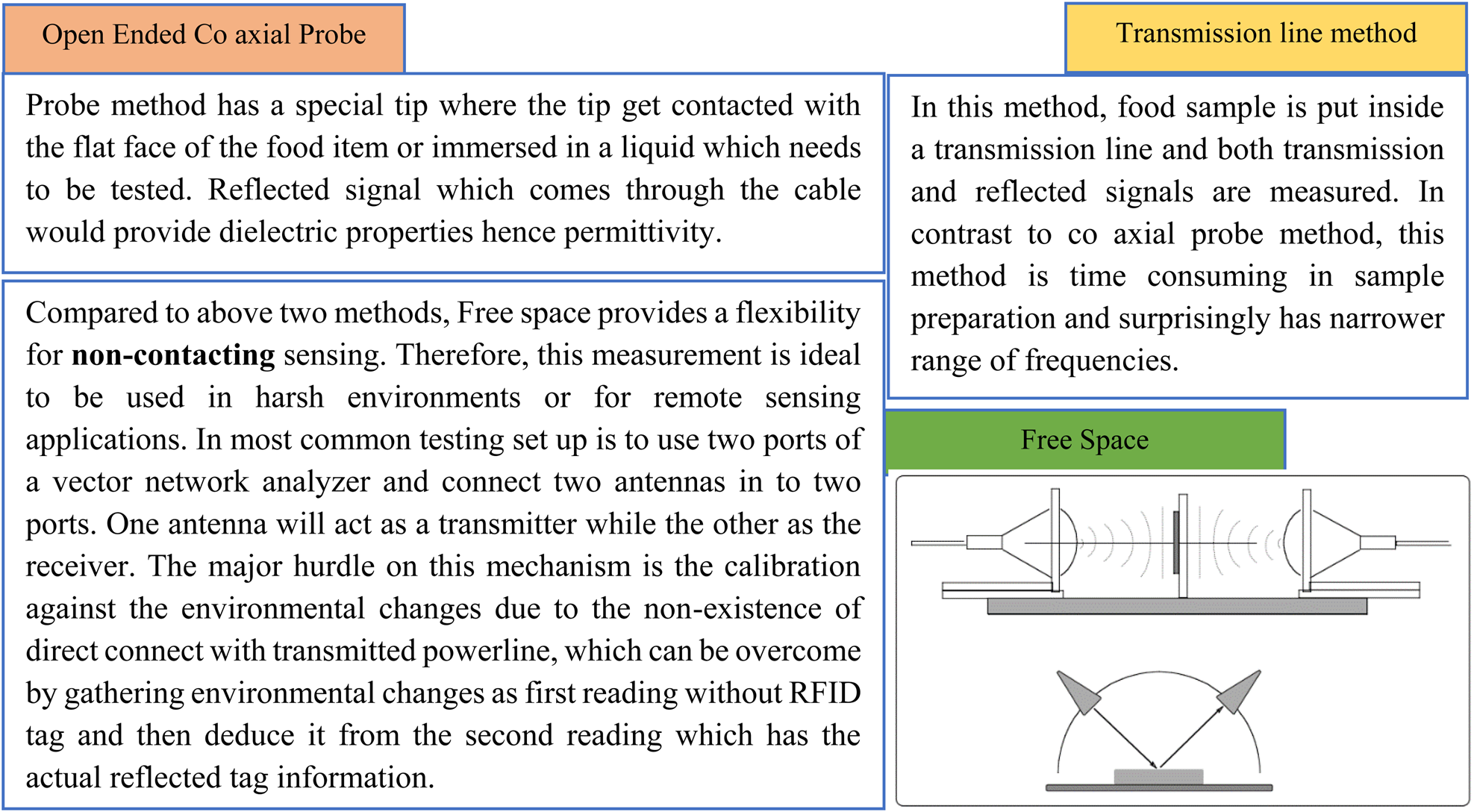







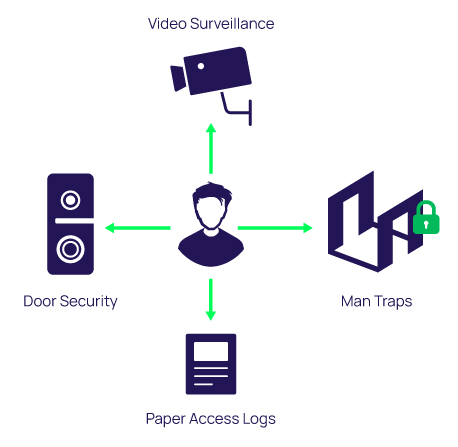
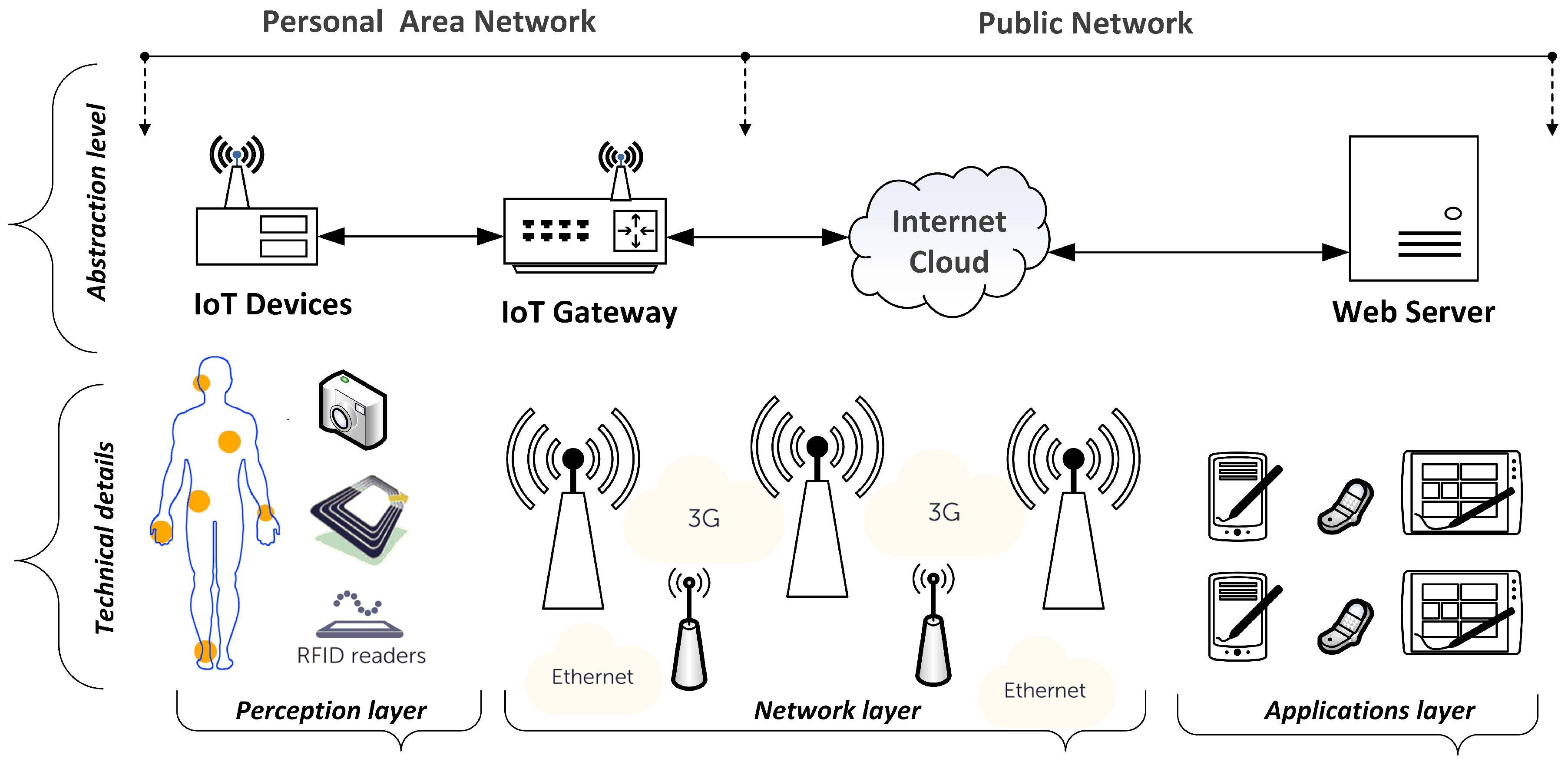


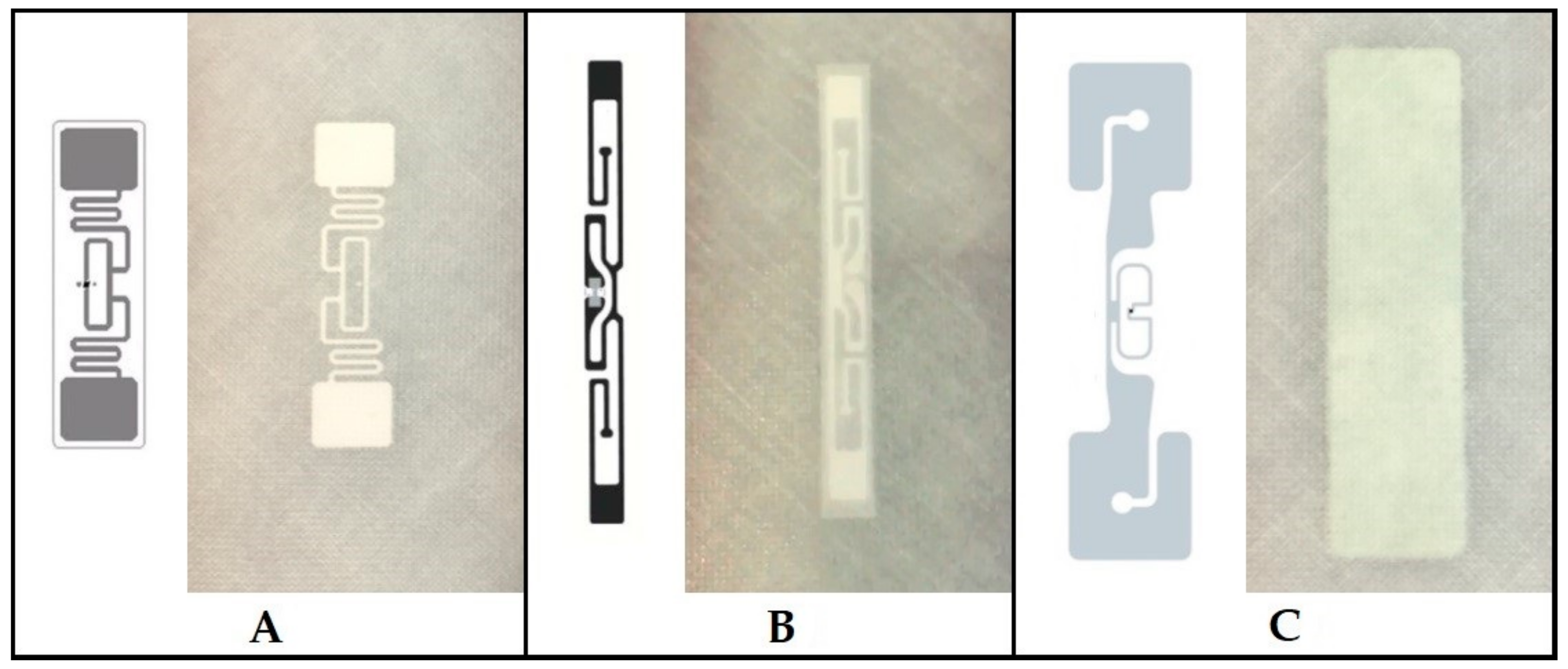








Post a Comment for "44 an rfid label on a box is an example of what type of physical security detection method"